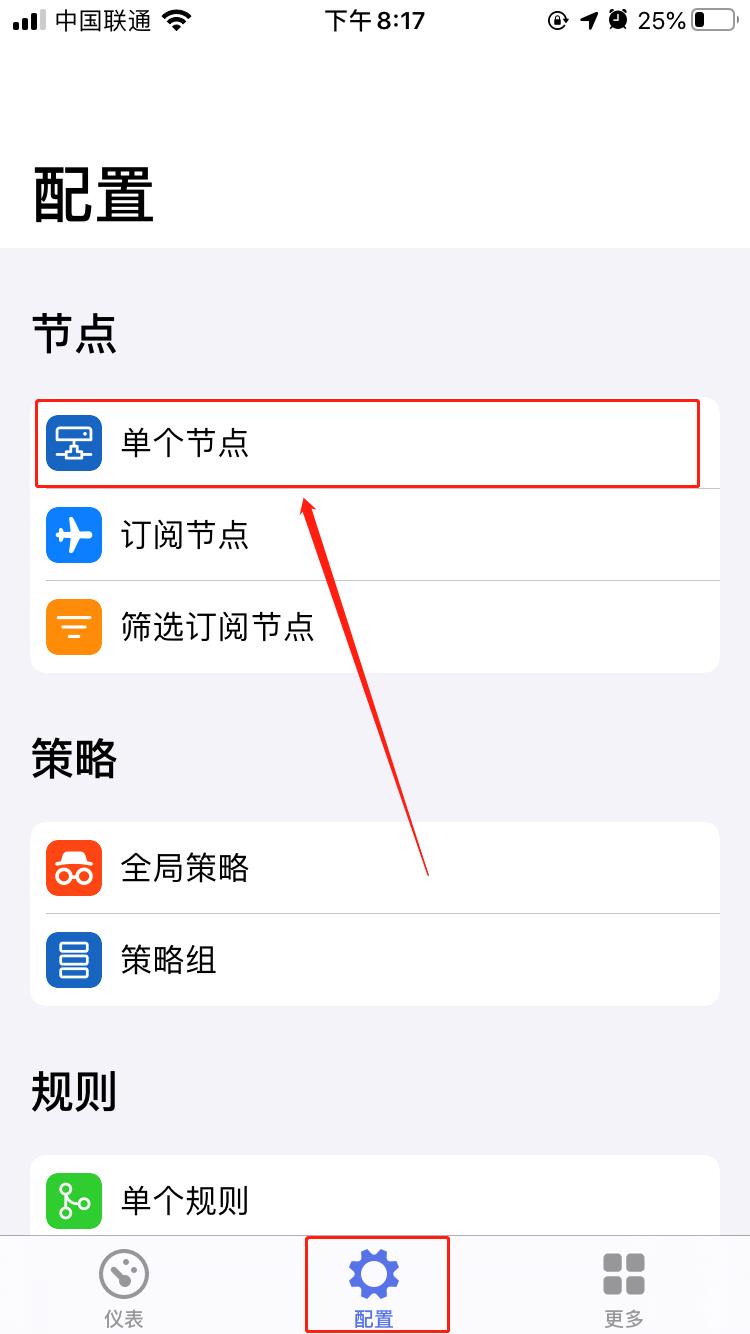
Single node
Users can add a self-built server through the single node button. A node represents a proxy server, and the proxy server can realize the transfer of traffic.
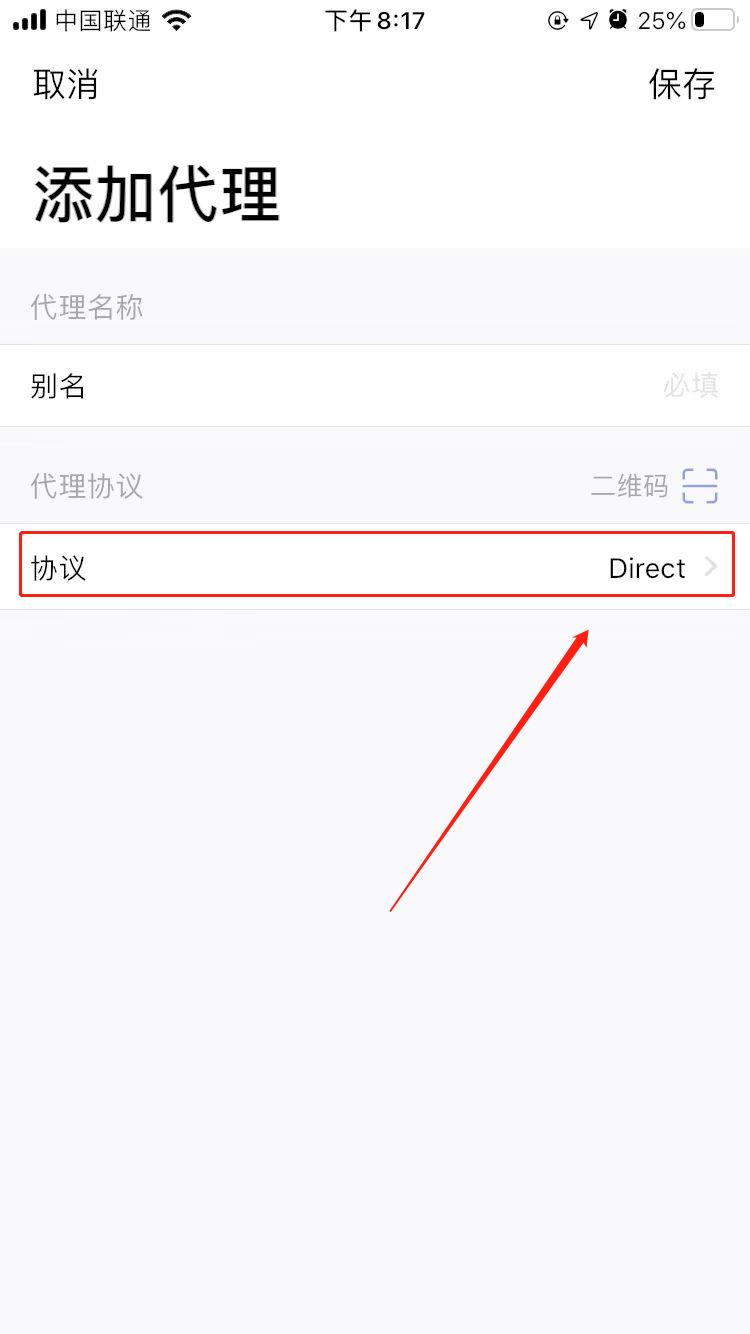
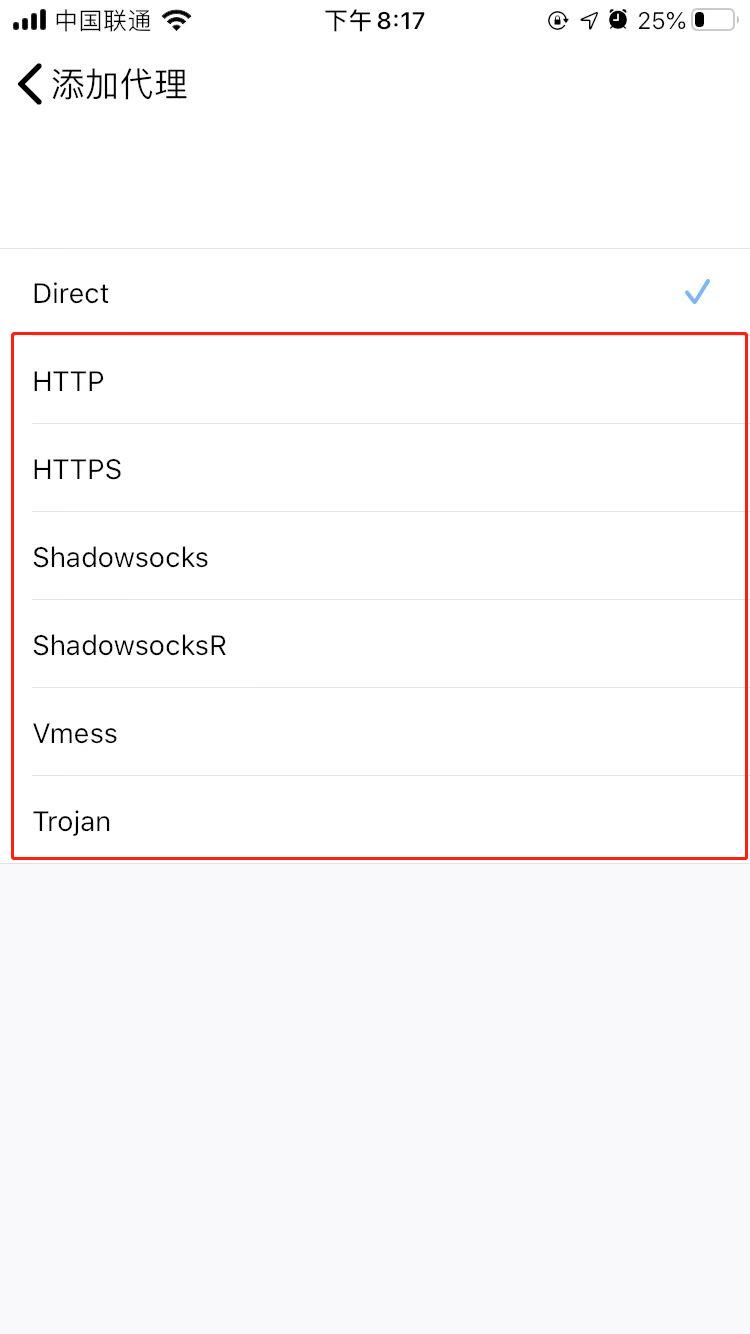
Currently supported protocols are
HTTP
HTTPS
SS
SSR
V2ray
Trojan
Add method
The first method: write through the UI

The second method: by writing in the configuration file or text editor
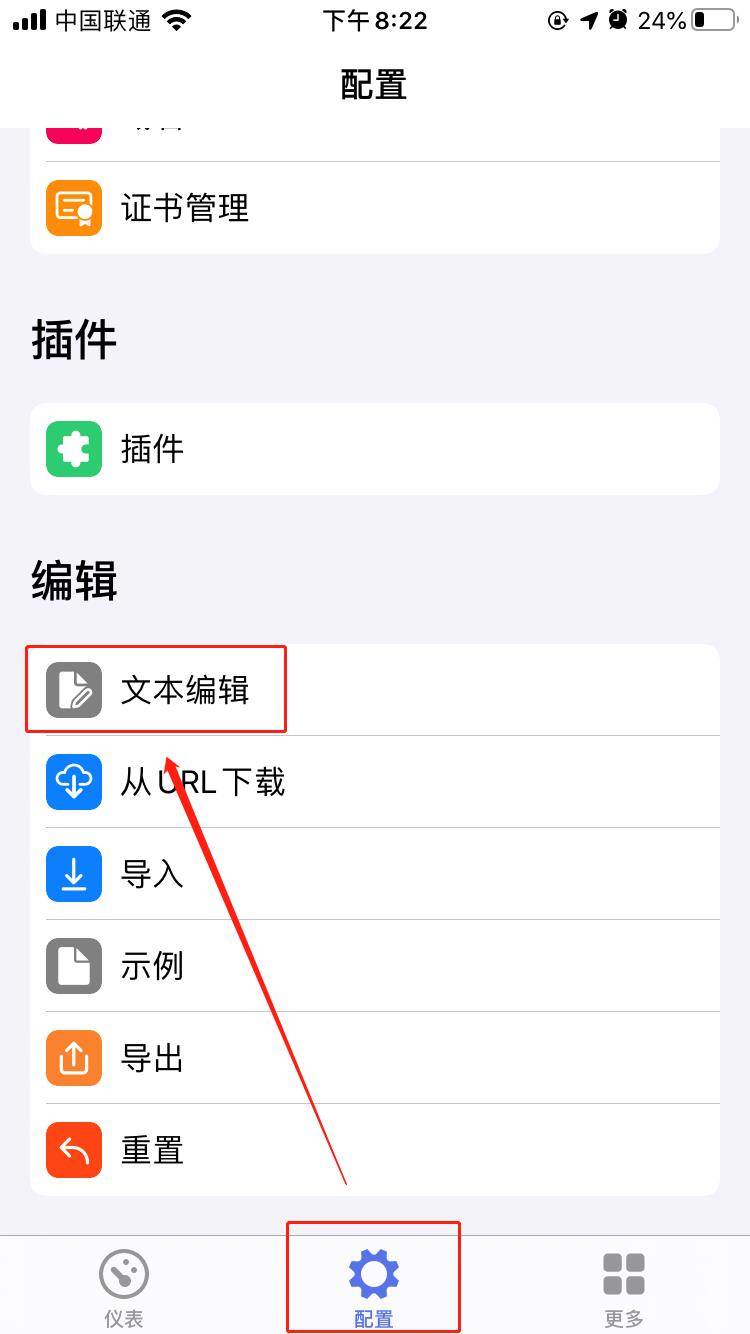
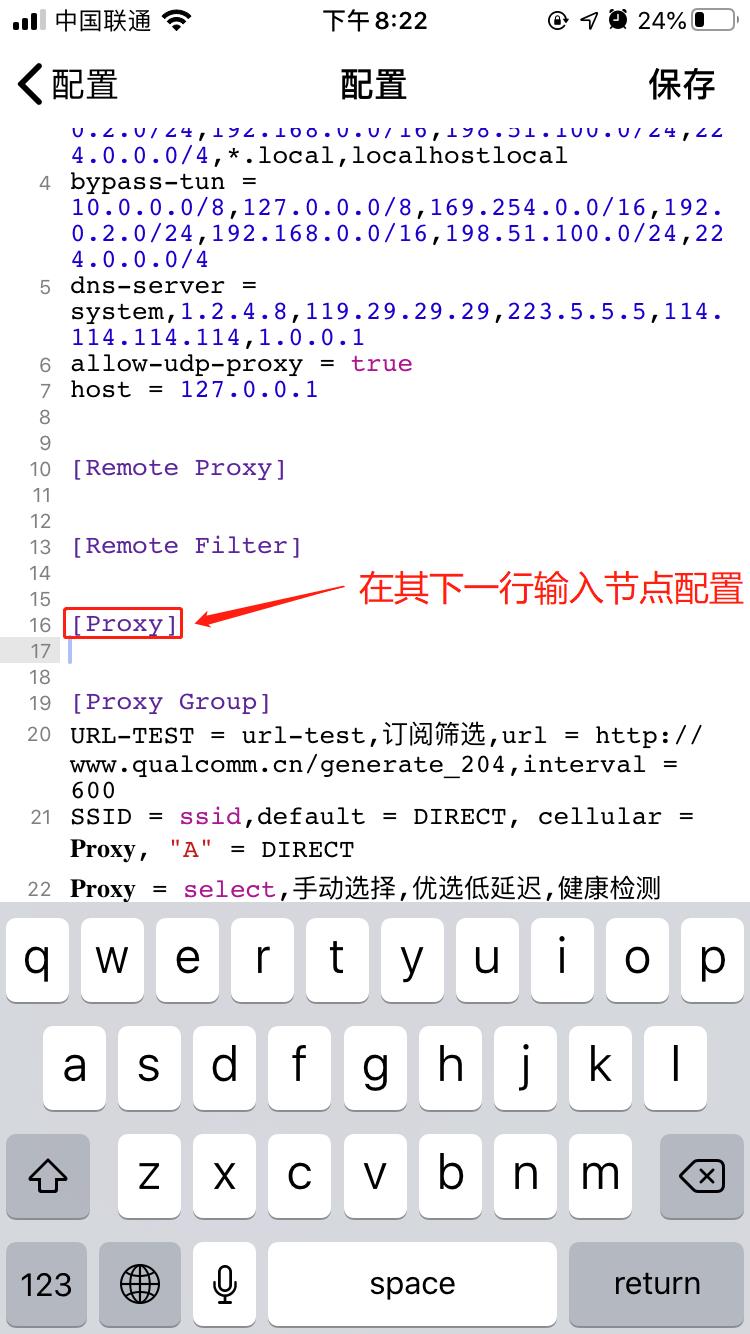
[Proxy]
# Built-in DIRECT, REJECT strategy
# http(s)
# Node name = protocol, server address, server port, user name, password
1 = http, 1.2.3.4, 443, username, "password"
2 = https, 1.2.3.4, 443, username, "password"
# ss(r)
# Node name = protocol, server address, server port, encryption protocol, password
1 = Shadowsocks, 1.2.3.4, 443, aes-128-gcm, "password"
2 = Shadowsocks, 1.2.3.4, 443, aes-128-gcm, "password"
3 = ShadowsocksR, 1.2.3.4, 443, aes-256-cfb,"password",auth_aes128_md5,{},tls1.2_ticket_auth,{}
4 = ShadowsocksR, 1.2.3.4, 10076, aes-128-cfb,"password",auth_aes128_md5,{},tls1.2_ticket_auth,{}
# vmess
# Node name = protocol, server address, port, encryption method, UUID, transmission method: (tcp/ws), path: path in the websocket handshake header, host: path in the websocket handshake header, over-tls: whether tls, tls-name: tls name, skip-cert-verify: whether to skip certificate verification (default is no)
6 = vmess, 1.2.3.4, 10086, aes-128-gcm,"uuid",transport:ws,path:/,host:icloud.com,over-tls:true,tls-name:youtTlsServerName.com,skip- cert-verify:false
# trojan
#Node name = protocol, server address, port, password, tls-name: tls name, skip-cert-verify: whether to skip certificate verification (default is no)
7 = trojan, 1.2.3.4, 443,password,tls-name:youtTlsServerName.com,skip-cert-verify:falseSay a few more words
- Due to different protocols, users need to write the configuration by themselves, this tutorial will not describe in detail
